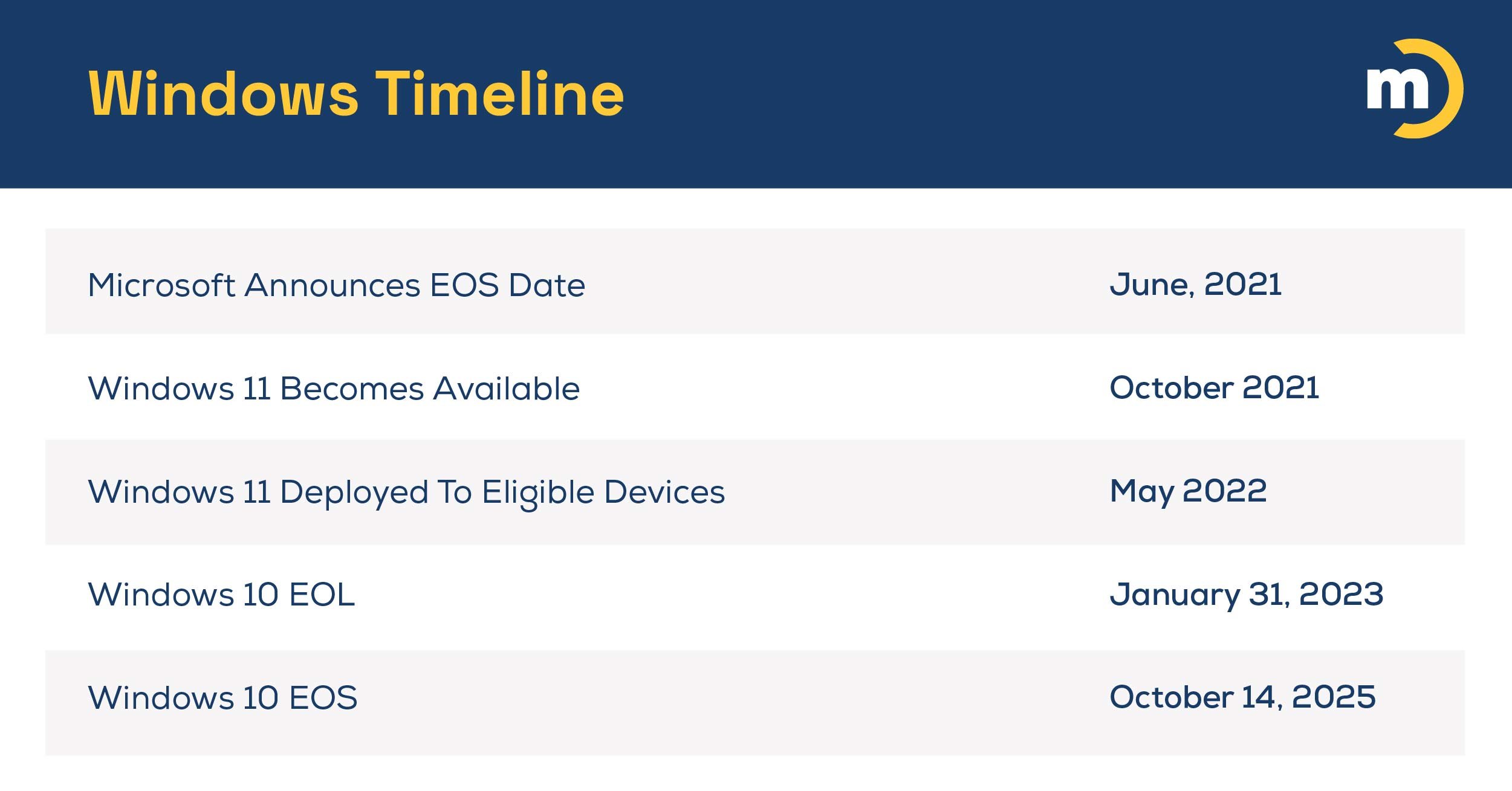
Secret (and Not-So-Secret) Ways To Simplify Microsoft Licensing for SMBs
Once upon a time, a small business could buy a Microsoft product and use it to its heart’s content. Okay, so that p…
Questions To Ask Before Purchasing a Production Printer
Does your organization need to produce a lot of printed materials? If you do a significant amount of print marketin…
Data Center Trends for 2024 and Beyond
You’re reading a technology blog to get a few quick answers. You happen to look at the publication date, and it’s f…
Is Printer Workflow Automation the Productivity Hack You’re Looking for?
If increasing productivity, reducing frustration, and reducing errors are wish list items for the year, a few diffe…
Should You Consider Outsourced IT Support for Your Small Businesses?
Generally speaking, the smaller the business, the tighter the budget. In a small business environment, employees mu…
Business Fraud Prevention: 101
Nowadays, business fraud is a big business. According to Alloy’s 2024 State of Fraud Benchmark Report, 56% of surve…
What’s Hosted Voice, and Why Should Your Business Use It?
There's just something satisfying about a landline telephone, and unlike the old dot matrix printer, many people st…
There’s an Easier Way To Do Procurement for K-12 and Higher Education
At first glance, an elementary school in Oregon wouldn’t have that much in common with an elite liberal arts univer…
Why Multi-Factor Authentication Is Important for Businesses
Passwords are a lot like keys. Some keys are better and more sophisticated than others, and a locked door is obviou…