Navigating VMware Licensing Changes: What You Need to Know Now
Two years after Broadcom completed its $69 billion acquisitionof VMware in November 2023, the licensing overhaul th…
Business Phone Systems for Manufacturing: What Actually Works
Traditional phone systems weren’t built for the way manufacturing actually works. They were designed for people sit…
5 Common Healthcare Cybersecurity Challenges (and How MDR/SOC Can Help)
In our conversations with healthcare clients, we hear the same five security challenges come up again and again. If…
Understanding Cybersecurity Threats to the Manufacturing Industry
In 2024, 26% of cyberattacks targeted the manufacturing industry. I'm not trying to be alarmist. But I am trying to…
What To Know About the 2026 Memory Chip Shortage
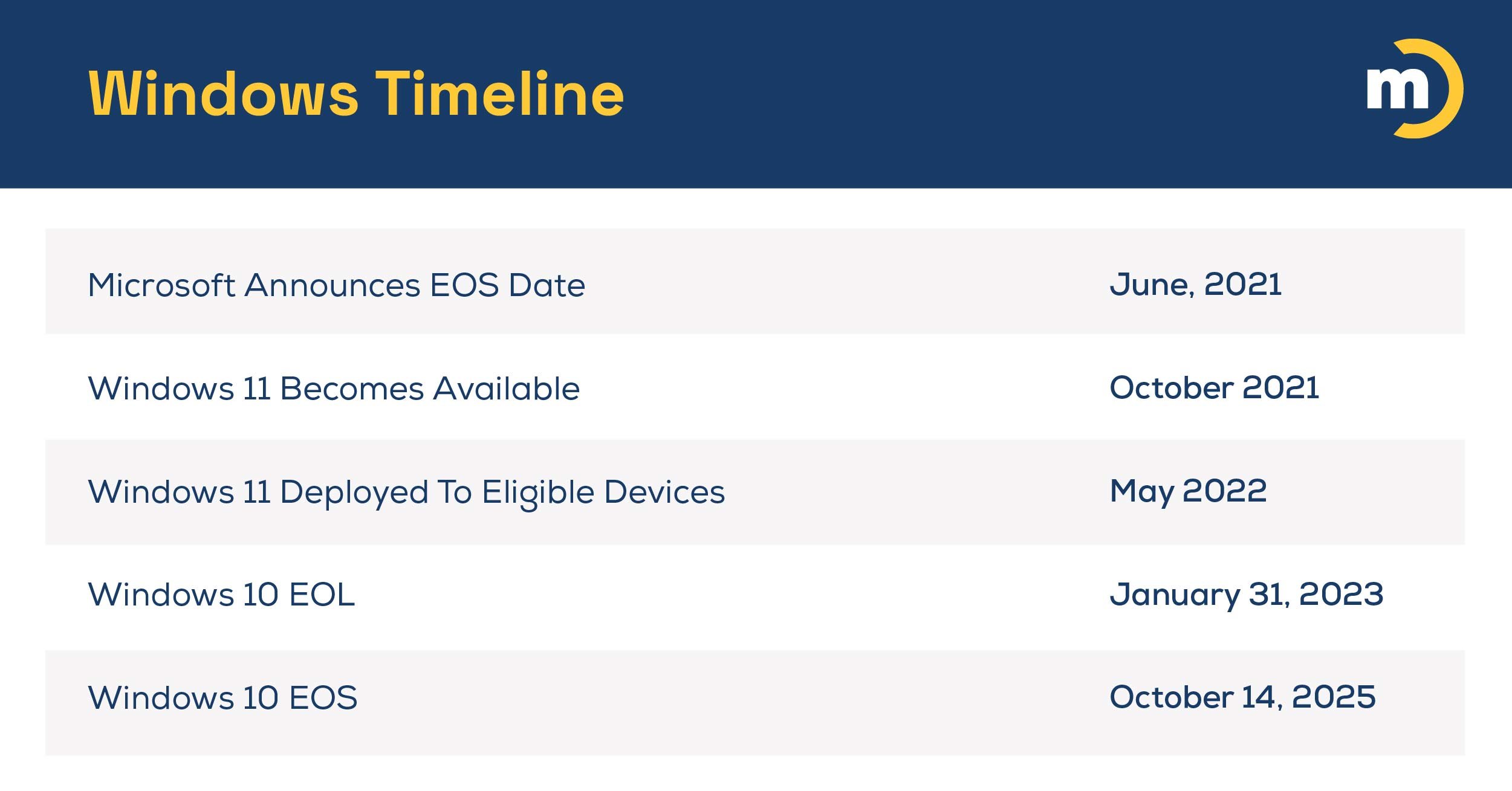
Still need to update some Windows 10 hardware or buy new servers? Our best advice is to make those purchases ASAP. …
What Law Firms Should Know About Meeting Cybersecurity Compliance
29% of law firms experienced a security breach in 2023, according to the ABA Cybersecurity TechReport. As someone w…
What Our Online Microsoft Insights Assessment Can Reveal
Microsoft has invested billions into cybersecurity, but users are still responsible for protecting their own data a…
How Managed Print Can Support Digital Transformation in the Finance Industry
The finance industry has a lot to gain from a digital transformation. It’s difficult to imagine a financial institu…
The Benefits of Managed IT Services for Manufacturing
Digital transformation promises enormous competitive advantages for manufacturers that are able to take advantage o…