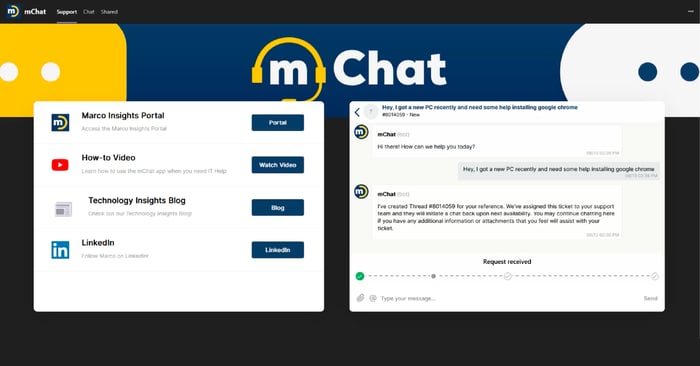
Revolutionizing IT Help Desk Support: Marco's New Chat-Based Solution
Every doctor or veterinarian we know has a similar issue — you want to be accessible to those who have urgent needs…
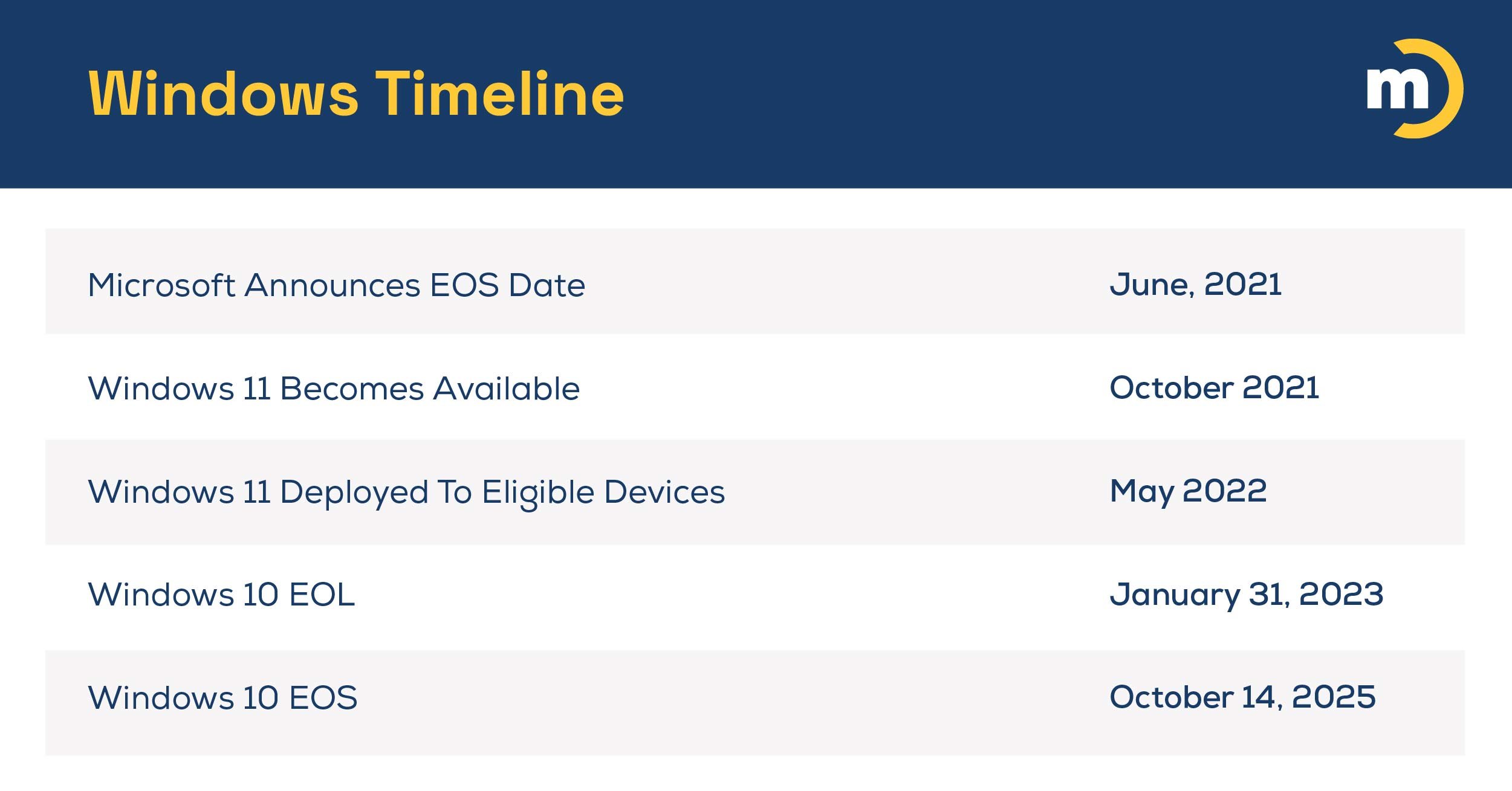
Windows 10 EOS: Three Paths Forward
October 14, 2025, has come and gone, marking the official end of support (EOS) for Windows 10 after a decade of ser…
Holiday Cybersecurity Best Practices
It’s tough to find someone who doesn’t enjoy the holiday season. Unfortunately, cybercriminals love it for many of …
What Businesses Should Know About Microsoft Teams Security
Let’s start with the good news. Microsoft has spent, and will continue to spend, billions of dollars on cybersecuri…
The Smart Response to Cisco Firepower’s EOL: Hybrid Mesh Firewall Explained
If your business relies on Cisco Firepower 1000, 2100, or 4100 series firewalls, it's time to start planning ahead.…
What Is Patch Tuesday and Why Should You Care?
You already know about Black Friday and Cyber Monday. But Patch Tuesday is more significant for the tech community,…
What Is Your Incident Response Plan?
What is your Incident Response Plan? An Incident Response Plan (IRP) should contain everything your organization wi…
Your Guide to Zebra Printer Troubleshooting
Zebra printers have a solid reputation for reliability even in harsh conditions. But even printers known for their …
5 Benefits of Desktop Virtualization Solutions
Back in the day, every computer required its own installation, preparation, and maintenance tasks, including patchi…