One of the most disgusting aspects of cybercrime is just how easy it is for criminals to make a killing from it.
Most cybercrime requires very little work on the criminal’s part. They don’t even have to acquire sophisticated hacking skills to carry out their attacks. Instead, they can carry out phishing scams and more in bulk. Even if they fail most of the time, even a small success rate adds up. That old Nigerian Prince email scam is frequently mocked for its clumsiness; nevertheless, it still pulls in a tidy profit each year.
However, cybercriminals are learning that with just a little more effort, they can fleece the public for much more. A new social engineering scam — pig butchering — is designed to fatten up victims before going in for the kill.
What Is Social Engineering?
In order to understand pig butchering, you have to understand what social engineering is and how it works. Social engineering is what criminals do to trick potential victims into revealing sensitive data or dropping their guard. Typically, criminals try to lure you in by piquing your curiosity, scaring you, or creating a sense of urgency.
But the aptly named pig butchering scam is a bit different — criminals are luring their victims by appealing to their sense of greed.
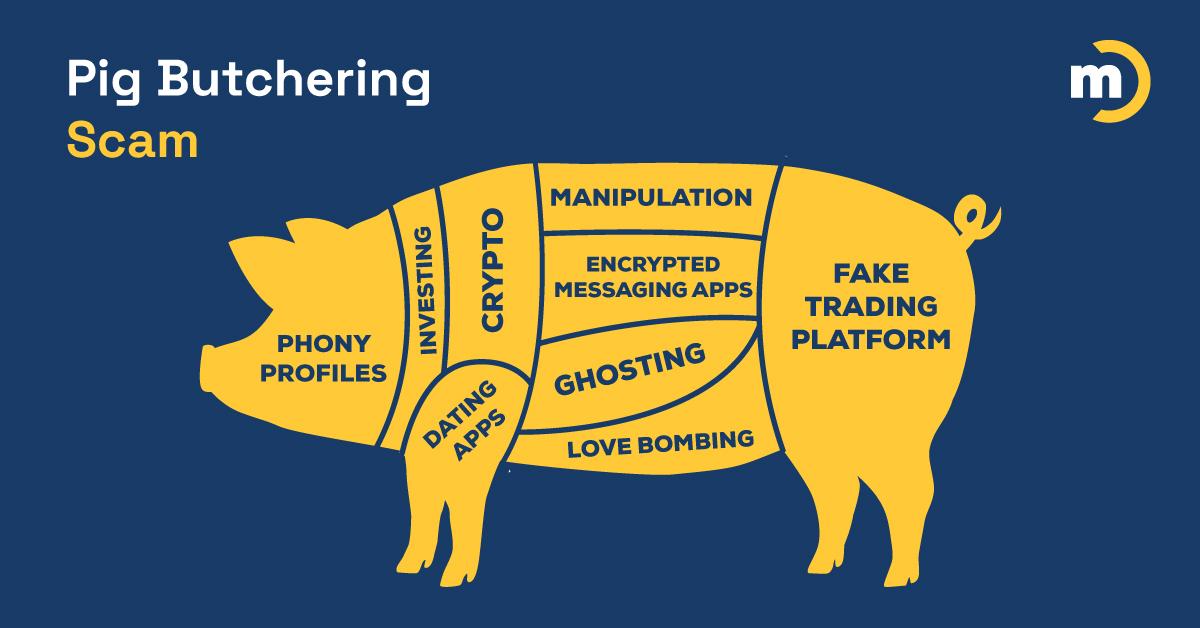
The 8 Steps in a Classic Pig Butchering Scam
But the aptly named pig butchering scam is a bit different — criminals are luring their victims by appealing to their sense of greed.
- A cybercriminal will try to befriend a potential victim through text or social media.
- Once the cybercriminal feels they have earned some trust, they will begin talking about a great cryptocurrency opportunity that has made them wealthy.
- If the potential victim is enticed by this story, the cybercriminal has found a new “pig.”
- The cybercriminal will direct them to an app or a website that will appear to be legitimate.
- Their victim will start by entering a small amount of money to test this “amazing investment” platform.
- The cybercriminal will show the funds as “fattening up” in value and even let the victim withdraw some of the money to build more trust in the platform.
- The victim eventually responds by going all in.
- The cybercriminal shuts down the platform — taking their victim for everything they’re worth.
Recent Scam News
Pig butchering scams have proven to be very successful for criminals. It was recently reported that just one pig butchering ring has stolen $505 million since 2018.
And if it feels like preventing cybercrime is falling, rather unfairly, on the shoulders of regular citizens, that’s because, for the most part, it is. The U.S. Department of Justice recently seized seven domains linked to pig butchering scams, but more pop up all the time. At this time, it’s more effective to warn people against scams like these than to focus entirely on tracking down these elusive scammers.
And, of course, pig butchering is only one way cybercriminals are cashing in. The cost of cybercrime is predicted to hit $8 trillion in 2023, according to Cybersecurity Ventures' 2022 Official Cybercrime Report.
How to Avoid Being a Social Engineering Victim
Think you are too smart to fall for a scam? If all scams were like the Nigerian Prince email, odds are that you’re right. But social engineering techniques are designed to overcome your natural skepticism, and criminals are also better at disguising their content, even eliminating the grammar and spelling errors that were once a dead giveaway. In fact, many criminals are probably taking advantage of composition tools like ChatGPT.
Without regular, robust training, a whopping six out of ten Americans are vulnerable to phishing scams. Training goes a long way, but cybercriminals are constantly evolving new scams and getting better at carrying them out. And as phishing scams are precursors to ransomware and more, a multi-faceted approach to cybersecurity is important for all organizations — even small to midsize businesses who may not consider themselves a target. SMBs are actually a favorite target of cybercriminals because their cybersecurity measures are not as robust.
Cybersecurity is always evolving, so if you’d like to give your organization a quick check-up, we’ve created a handy checklist specifically designed for small businesses to make sure they’re in line with industry best practices.
If you have any questions as you’re going through it, let us know! Our US-based team is passionate about protecting businesses from cybercriminals, and while we are always here for those who have been the victim of an attack, we’d much rather prevent that attack from ever taking place.
