There has been quite a bit of talk – and jokes – about the “Russian attackers” in recent days. So is the threat real and how does it impact your organization?
Russian hackers claim they will try to disrupt the U.S. election (as if it is not already disrupted by the presidential candidates). Last week, the Obama administration claimed that senior Russian officials authorized hacks into the Democratic National Committee and tampered with online voter registration. Experts responded by saying that the impact is likely more psychological.
But the threat is real. You can actually see attacks happening this second at map.norsecorp.com. There’s a war going on out there that most never see.
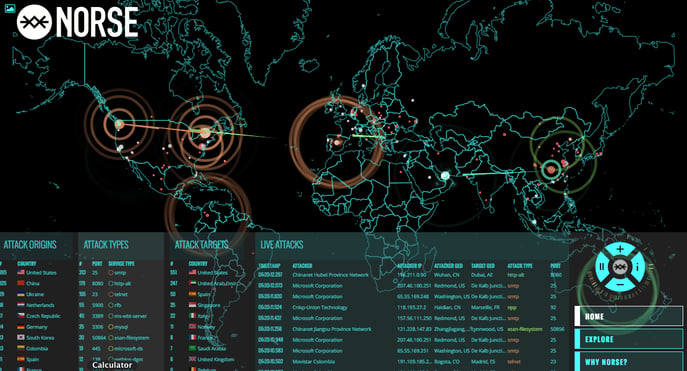
The threats are increasing in both their severity and frequency. You can easily find a hacker’s kit on the Internet and start using it. A rising number of people are making money through hacking and exploiting people. (Go ahead and Google it, but don’t click.)
New Attacks
The term “hackers” is quite broad, covering everything from the development of crypto lockers, worms and other forms of malware to attempts to take down systems using methods like a distributed denial of service attack, known as DDoS attacks. (See how to protect against malware attacks.)
In the case of DDoS attacks, hackers prey on devices that operate on the edge of your network. That’s everything from the new smart refrigerators to sensors, surveillance cameras, IP telephony and wireless access points.
They find an unprotected device and then use it to complete the attack. The rise of the Internet of Everything (IoE) enables hackers to use millions of devices at one time to attack an IP address, so they cannot be stopped easily during the process. That means your business could look like it is hacking another system – until it is traced back to Russia. Yes, it’s crazy.
How do you protect yourself from DDoS attacks? Much of the protection comes from how your security architecture is set up. Think of it like an onion – with a variety of layers. Organizations of all sizes now need a comprehensive security program. Here’s a look at what that includes:
PART 1: Layers of Protection
- Firewall: Begin with a strong, external facing layer of protection with a firewall that establishes limited access to the inside of your network (onion). Keeping your firewall software up to date is critical. When it gets out of date, it can be just like not having one at all.
- Intrusion Detection System: This device or application monitors your network or systems for malicious activity or policy violations and alerts your system administrator.
- Intrusion Prevention System: Like an intrusion detection system, this system monitors network traffic. However, because an exploit may be carried out very quickly after the attacker gains access, intrusion prevention systems also have the ability to take immediate action, based on a set of rules established by the network administrator.
- Mobile Device Management: This software system allows you to monitor and manage mobile devices on the network, including limiting access and even locking or wiping phones in case of a breach.
PART 2: Testing and Evaluation
Test your plan to ensure the policies and procedures you have outlined are being met. Often times, organizations bring in a third-party technology advisor to assist. When we are the ones managing clients' networks, we ask another company to conduct penetration testing.
While this has become a requirement in some industries, such as financial, it is a good practice for any type of organization of any size. It includes everything from assessing access points to physically viewing the systems. Is the server door locked? Can someone get your admin password? Essentially, we try to break in and test each policy.
PART 3: Educate End Users
Most security breaches come from within an organization. An employee inadvertently clicks on a malicious link or plugs a device into the system that contained a virus that takes it down. (See how to protect against email hacks.)
One of the best lines of defense is education. Help your users understand how to use technology safely. Educate them on the policies and procedures you have in place – and even test their adherence to them.
Every organization is at risk and the risk is real. Don’t brush it off and think it won’t happen to you. Protect your organization. You have too much at stake and we need more organizations stepping up to prevent hacks.
